Unauthorized access to networks is currently one of the most serious threats to the hosting business. Intruders and viruses present the two biggest security threats to the industry. Let us examine three key definitions: intruders (or hackers), intrusion, which is a formal term for describing the act of compromising a network or system, and Intrusion Detection Systems, which help business detect when they are vulnerable to an attack.
Intruders can be external or internal and their intents may vary from benign to serious. Statistically 80 percent of security breaches are committed by internal users and these are by far the most difficult to detect and prevent. These intruders create a significant issue for network systems and IT equipment. Intruders come in a variety of classes with a varying level of competence -- an external user without authorized access to the system will want to penetrate the system to exploit legitimate user accounts to access data, programs or resources with a purpose of misuse. Intruders may even use compromised systems to launch attacks.
Examples of intrusions that may vary from serious to benign:
1. Installing and making unauthorized use of remote administration tools
2. Performing a remote root compromise on the Exchange server
3. Defacing a Web Server
4. Using sniffers to capture passwords
5. Guessing or cracking the passwords
6. Noting the credit card details from a Database
7. Impersonating a user to reset or gain access to the password
8. Using unattended and logged on workstations
9. Accessing the network during off hours
10. Email access of former employees
Defining an Intrusion Detection System
An intrusion detection system (IDS) is a device or application that monitors all inbound and outbound network activity and identifies suspicious patterns that may indicate a network or system attack from someone attempting to compromise the system. It is an intelligent system which is deployed on the physical layer in a network which then monitors any unauthorized intervention to the environment. An IDS is based on the assumption that the intruder behaves differently from that of any authorized users and these activities can be quantified. The following discusses the approaches to intrusion detection:
Statistical anomaly threshold detection
The approach where data is collected relating to the behavior of a legitimate user. The data and the threshold are defined along with the frequency of occurrence for various events.
Statistical anomaly detection -- Profile based is the approach where the data is collected relating to the behavior of a legitimate user. A profile of activity is created of each user and is then developed for further use to detect any significant behavior that would lead to a suspicious act.
Rule based anomaly detection
This detection method defines the set of rules that can be used to define the type of behavior of an intruder. These rules may represent past behavior patterns (of users, devices, timelines, etc.) which are matched to the current patterns to determine any intrusion.
Rule based penetration detection is an expert system that defines a class of rules to identify suspicious behavior even when the behavior is confined to the patterns already established. These rules are more specific to the devices or the operating system.
The prime difference is that the statistical approach attempts to define the normal or expected behavior and rule-based approach focuses on way the way the user navigates its way around the system.
Below are some measures that are used for intrusion detection:
1. By analyzing the login frequency of the user by day and time, the system can detect whether the intruder is likely to login during out–of-office hours.
2. By measuring the frequency of where the user logs in and at which specific locations, an IDS can detect whether a particular user rarely or never uses that location
3. By measuring the time between each login, an IDS can verify whether a dead user is performing an intrusion
4. The time elapsed per session, including failures to login, might lead an IDS to an intruder
5. The quantity of output to a location can inform an IDS of significant leakage of sensitive data
6. Unusual resource utilization can signal an intrusion
7. Abnormalities for read, write and delete for a user may signify illegitimate browsing by an intruder
8. Failure count for read, write, create, delete may detect users who persistently attempt to access unauthorized files.
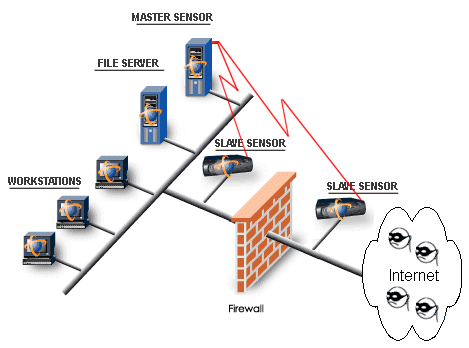
Here’s how it works with an IT network
How can I protect myself?
Intrusion detection systems use a variety of methods and the goal of each is to identify the suspicious activities in different ways. There are network based IDS (NIDS) and host based IDS (HIDS). As the name suggests the network based IDS is strategically placed at various points in a network so that the data traversing to or from the different devices on that network is monitored. The network based IDS checks for attacks or irregular behavior by inspecting the content and the header information of all the packets moving across the network. Host based IDS refers to intrusion detection that takes place on a single host system. These are aimed at collecting information about the activity on a particular host which are also referred to as sensors. Sensors work by collecting data about events taking place on the system being monitored. Both types of IDS have unique strengths, and while the goal of the two types of IDS is the same, the approach differs:
Host based IDS:
- Monitors specific activities
- Detects attacks that are missed by network IDS
- Provides near real time detection and response
- Requires no additional hardware
Network IDS:
- Is independent of the operating system
- Provides real time detection and response
- Is difficult for the intruder to remove evidence
- Detects attacks that are missed by host based IDS
Vivek Vahie is senior director of service delivery at NaviSite.
Picture credit: alphaspirit/Shutterstock
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.