Regardless of whether you’ve been hit with ransomware or not, protecting your network from these types of attacks is now an integral part of any network security framework for both individuals and companies. Protecting yourself from intrusions and attacks requires securing your main layers of defense by utilizing Security Awareness Training and antivirus/anti-phishing software.
If you consider a computer network (even a simple one, like your home computer) to consist of a series of layers that any malware or virus needs to penetrate, the outermost layer would consist of your users themselves. After all, it takes a user’s interaction in order to initiate or allow a network intrusion. Only AFTER a user has clicked or visited a malicious link, will your secondary and tertiary layers (firewalls and antivirus) come into play. Thus, the very first layer you will need to harden is that of the human operator. It is only in recent years that the importance of this layer of security has come to be recognized. In the past, software has been relied upon as a catch-all for these types of situations. Software just by itself is not enough anymore, users must be trained to prevent such attacks from happening in the first place.
Security Awareness Training
Yes, this is the part of the article where we tell you that you need to implement effective Security Awareness Training.
People are used to having a technology solution [but] social engineering bypasses all technologies, including firewalls. Technology is critical, but we have to look at people and processes. Social engineering is a form of hacking that uses influence tactics.
-Kevin Mitnick
Despite evidence to the contrary, users do not come to work with the intention of clicking on phishing emails and infecting their computers! As many IT professionals can attest, a simple knowledge of what red flags to be aware of can make a huge difference in the ability of a user to discern malicious links/software from legitimate traffic. As the methods hackers and malware creators use to trick users are constantly changing, it is important to keep users up-to-date on not only the basics of IT and email security, but also the ever changing attack types and threat vectors. After all, everyone knows that there is no Nigerian prince out there and it’s just a scammer right? But what if "Becky" from the "accounting firm" accidentally sends you a payroll spreadsheet? Not everyone is going to question the ambiguous origin of a well-crafted phishing email, especially with a juicy attachment like Q4 Payroll.zip. HR may receive 20 resumes a day, but only one of those needs to be malicious to cause an incident.
Increasingly, hackers and attacks utilize "social engineering" to entice or trick a user into installing or opening a security hole. KnowBe4 Security Awareness training covers not only software based threat vectors and red-flags, but physical security training as well. User security training is a vital piece of securing your network.
Simulated attacks
While training can have a big impact on hardening the first layer of security, it is the one-two punch of training combined with simulated phishing attacks that can create a constant state of users being on their toes with security top of mind which that will make it extremely hard for any phishing attempt or email-based attack to succeed.
Today, with KnowBe4’s simulated phishing campaigns, you can send fully randomized and completely customizable simulated phishing attempts to any number of users in your environment. It is important that your users are constantly on the lookout for these attacks.
After all, if they know that the organization is phishing them, they will pay extra attention to what is coming through their inbox. Users can no longer rely on "the antivirus" or "IT" to handle any slip-ups -- they are being actively tested! Also, any lapses or errant clicks can be used as opportunities for further training on what types of red-flags to be aware of. The consequence of clicking on a simulated phishing email is far less destructive than the alternative.
Another benefit of simulated phishing attacks is immediate inoculation against current threats. For example, you can use simulated phishing attacks to get an accurate idea of how your users will respond to malware and phishing emails that are actually being used by ransomware developers to infect systems. This way, you can immediately detect vulnerabilities and educate users on current threats so they know what to watch out for. KnowBe4 keeps an updated list of ransomware and current event email templates that you can use to check for any phish-prone users in your environment.
Software based protection: Anti-Virus, Anti-spam/phishing & Firewalls
One simply cannot operate a computer these days without a software based protection in-place. It is vital even for stand-alone computers to utilize this software. In fact, it is almost assured that you or your organization are already utilizing one or more of these solutions. While I could go on for ages about the whys and wherefores of various security software, the focus here is on Ransomware. As a result, I am going to point out some particular software solutions to this issue that can be implemented.
First, Microsoft has a feature called Software Restriction Policies that can be used in a secure environment to ONLY allow certain software as (defined in the policy) to run. There are certain directories that ransomware infections will typically start in, and by isolating these directories with a software restriction policy, you can cut down on the susceptibility of infections.
For more information on Software Restriction policies, see this Ransomware Knowledgebase.
Another option for reducing the chance of ransomware infections (on top of your existing antivirus solution) is to use a specialized software for scanning for these types of infections.
Microsoft has developed a Cryptowall active alerter/scanner which will actively scan for ransomware-type activity and alert users. It is more advanced in use and not intended for home users. You can find it here.
For a list of ransomware-specific prevention applications, see this Ransomware Knowledgebase.
Backups
The last piece of the puzzle in any ransomware protection must include a regular backup of your files as well as a regularly TESTED restore procedure.
With so many options available for both on-site backup solutions and cloud-based backup solutions, there is no reason any user or company should not have a very regular backup of files. To help prevent your backups being compromised, you should always have an off-site or redundant backup in place. If your backups are easily accessible by a computer infected with ransomware, don’t be surprised if your backups are encrypted as well! Having off-site and recent backups is a standard "best practice" for backup procedures against ransomware.
An often overlooked part of any backup procedure is testing that your restoration of files actually works! There is nothing worse than discovering an old hard-drive or DVD that you burned with backups is now unresponsive or malfunctioning. Always ensure you have adequate and fast enough access to your backup sources and a function restoration method in place. "I have DropBox" is not an adequate backup solution. While DropBox does have versioning, is is not a backup service and recovering older versions of your files from common cloud based storage such as DropBox, Google Drive and OneDrive can be a very tedious or time-consuming task as they are not set up or designed to be a backup service.
I've written an informative complete manual on beating ransomware, which you can download from here. The free Ransomware Hostage Rescue Manual is packed with actionable info that you need to have to prevent infections, and what to do when you are hit with ransomware. It also includes a Ransomware Attack Response Checklist and Ransomware Prevention Checklist.
Image Credit: Robynrg/Shutterstock
 Stu Sjouwerman is the founder and CEO of KnowBe4, which hosts the world’s most popular integrated Security Awareness Training and Simulated Phishing platform. Realizing that the human element of security was being seriously neglected, Sjouwerman teamed with Kevin Mitnick, the world’s most famous hacker, to help organizations manage the problem of cybercrime social engineering tactics through new school security awareness training. Sjouwerman is the author of four books, with his latest being Cyberheist: The Biggest Financial Threat Facing American Businesses.
Stu Sjouwerman is the founder and CEO of KnowBe4, which hosts the world’s most popular integrated Security Awareness Training and Simulated Phishing platform. Realizing that the human element of security was being seriously neglected, Sjouwerman teamed with Kevin Mitnick, the world’s most famous hacker, to help organizations manage the problem of cybercrime social engineering tactics through new school security awareness training. Sjouwerman is the author of four books, with his latest being Cyberheist: The Biggest Financial Threat Facing American Businesses.












 Edinburgh council was the target of a cyberattack this week, and the details of more than 13,000 email addresses were stolen. The council was quick to
Edinburgh council was the target of a cyberattack this week, and the details of more than 13,000 email addresses were stolen. The council was quick to 



 Stu Sjouwerman is the founder and CEO of KnowBe4, which hosts the world’s most popular integrated Security Awareness Training and Simulated Phishing platform. Realizing that the human element of security was being seriously neglected, Sjouwerman teamed with Kevin Mitnick, the world’s most famous hacker, to help organizations manage the problem of cybercrime social engineering tactics through new school security awareness training. Sjouwerman is the author of four books, with his latest being Cyberheist: The Biggest Financial Threat Facing American Businesses.
Stu Sjouwerman is the founder and CEO of KnowBe4, which hosts the world’s most popular integrated Security Awareness Training and Simulated Phishing platform. Realizing that the human element of security was being seriously neglected, Sjouwerman teamed with Kevin Mitnick, the world’s most famous hacker, to help organizations manage the problem of cybercrime social engineering tactics through new school security awareness training. Sjouwerman is the author of four books, with his latest being Cyberheist: The Biggest Financial Threat Facing American Businesses.
 There is also a new available background, which I applied on both the lockscreen and homescreen. This one is quite nice. This is not the only thing that is new while browsing the Settings menu, with Apple making some welcome changes in this area. The cellular settings are better grouped now, the battery information gets it own dedicated sub-menu which exposes a battery saving option, there is now an option to auto-lock the device after just 30 seconds (the previous-lowest was one minute), and new Siri-related options.
There is also a new available background, which I applied on both the lockscreen and homescreen. This one is quite nice. This is not the only thing that is new while browsing the Settings menu, with Apple making some welcome changes in this area. The cellular settings are better grouped now, the battery information gets it own dedicated sub-menu which exposes a battery saving option, there is now an option to auto-lock the device after just 30 seconds (the previous-lowest was one minute), and new Siri-related options.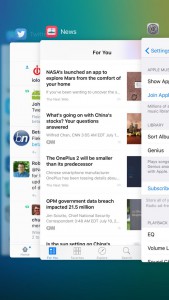 What I do not like about multitasking and switching apps is the new multitasking menu, which now shows apps stacked on top of each other instead of next to each other. There is too much focus on a single app. You can, however, still close multiple apps at the same time by swiping up with three fingers. And it looks prettier, which is a good thing in my book.
What I do not like about multitasking and switching apps is the new multitasking menu, which now shows apps stacked on top of each other instead of next to each other. There is too much focus on a single app. You can, however, still close multiple apps at the same time by swiping up with three fingers. And it looks prettier, which is a good thing in my book.