During a cyber attack, every second counts. While an attack can happen in an instant, it can take months to remove it from an organization’s infrastructure. For some organizations, there can be more attacks in one hour than a well-staffed security team can address in an entire day. That's a big problem.
Historically, attackers have had the advantage over defenders by being able to choose from a broad array of tools, around-the-clock attack windows, and innumerable attack types. If one type of attack failed, an attacker could simply try again and again until vulnerabilities were discovered. Moreover, cyber attacks are easy to organize and cheap to enact.
Any computer anywhere can become the front line of an attack, which is not only difficult to defend against but leads to the need for constant vigilance and flexible defensive moves. Attacks often come in looking like one piece of software code only to rapidly mutate and adapt to the target environment, proliferating at machine speed to expose weaknesses.
Because bad actors currently have the upper hand in cyber warfare, organizations need to find effective, innovative ways to combat them. They need speed. They need the power and control to change networks on the fly. They need to respond in seconds. They need to shift dynamically to spoof attackers with defensive tactics that appear as random to malicious actors as attacks so frequently appear to them.
Popular technologies such as firewall, antivirus, encryption, and authentication tools provide basic layers of protection, but they do not adapt in real time to combat malware that is infinitely flexible, adaptable, and patient. Instead, they behave like stationary sentries, unable to move, pivot, or otherwise adjust to an intruder whose infiltration tactics shift in milliseconds. These tools perform the grunt work of detection and protection, but when attacks come in looking like legitimate network traffic, how can the system detect them? How can a system know what to defend against when the code behind the attack can change its approach at will and at machine speed to escape detection?
Today's state-of-the-art security operations require well-honed protocols, advanced data gathering and analysis tools, and modern threat-identity infrastructures. But integrating multiple point security tools is expensive and does not scale when the tools are supported by manual processes. Security teams need a way to tie their tools together with proven processes and protocols and a dose of automation to make everything work at machine speed.
Smart organizations are building incident response plans with digitized cyber playbooks to support automated and semi-automated courses of action that can be synchronized across the security ecosystem. Playbooks are powered by automation and orchestration tools that enable security teams to counter attacks using coordinated defensive strategies; they contain all of the relevant workflows, tools, and processes necessary to respond quickly to a cyber threat.
Instead of analyzing and reacting to specific attacks as they happen, these forward-looking organizations maintain playbooks of active responses built from the proven protocols they use on a regular basis. An intuitive and effective playbook outlines courses of action and orchestrates them to execute specific threat-response scenarios, which allows organizations to reuse proven automation tools and workflows within larger threat-response strategies.
Over time, such playbooks can become digital libraries of approved actions that can be linked together to create active defense environments. Playbooks can continually collect organizational wisdom around security measures and provide security analysts with tested and adaptable sets of responses to multiple attack scenarios.
The use of playbooks offers immediate benefits to security teams, in part because automation tools allow them to keep pace with all incidents that penetrate the network. Orchestrated automation reduces the backlog of security incidents and decreases risk to network and data assets. It also enables security analysts to determine which issues pose the most threat or require the most investigation. Combining incident response plans with digitized playbooks allows organizations to automate repeatable processes that shore up the weak links in the security chain, which in turn enables highly trained staff analysts to focus on taking the steps necessary to maintain a continuously secure operating environment.
After all, many highly-specialized analysts spend significant amounts of time dealing with the manual aspects of the many advanced tools at their disposal. Countless personnel resources are expended on updating helpdesk tickets, uploading malware protections, testing hyperlink safety, and gathering information from infected machines.
In fact, many organizations spend more time on repeatable manual tasks than they do on analyzing actual incidents or supporting more advanced security measures.
Playbooks and other tools in the threat-response framework combine an organization’s best personnel, processes, tools, and workflows and organize them into a dynamic, flexible, real-time security-response engine, forming the cornerstone of a more effective and holistic security strategy. And in a world where organizations fend off millions of attacks every, speed and agility matter.
Paul Nguyen is president of CSG Invotas
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.






 Out of nowhere,
Out of nowhere, 

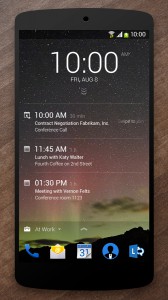 Microsoft app launches are usually predictable. Most are offerings which aim to get us hooked on the software giant's most-prominent products, like Office, OneDrive, Outlook.com and Xbox. But, every once in a while, Microsoft does something out of the ordinary, like it wants to tell the world that, much like startups, it too is capable of intriguing and exciting things.
Microsoft app launches are usually predictable. Most are offerings which aim to get us hooked on the software giant's most-prominent products, like Office, OneDrive, Outlook.com and Xbox. But, every once in a while, Microsoft does something out of the ordinary, like it wants to tell the world that, much like startups, it too is capable of intriguing and exciting things.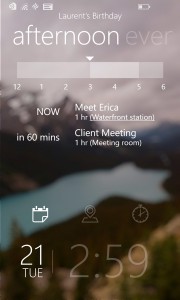 For Windows Phone users, Microsoft launched Tetra Lockscreen. It is very different compared to the stock Windows Phone lockscreen, that is still very sparse feature-wise, and the ones offered by Microsoft through its Live Lock Screen beta app, as, like Next Lock Screen, it shows a tremendous amount of information.
For Windows Phone users, Microsoft launched Tetra Lockscreen. It is very different compared to the stock Windows Phone lockscreen, that is still very sparse feature-wise, and the ones offered by Microsoft through its Live Lock Screen beta app, as, like Next Lock Screen, it shows a tremendous amount of information.




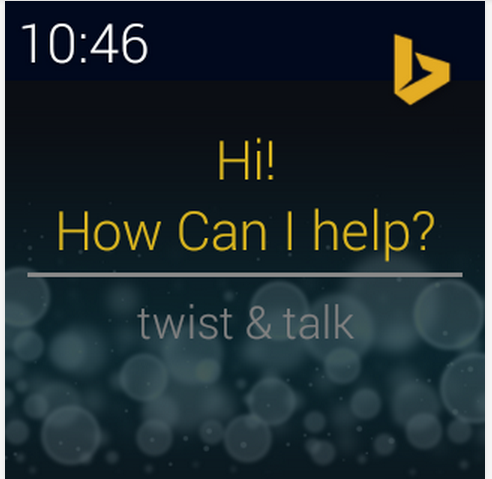
 When the smartwatch concept started to take off, I was dubious to say the least. I mean, I own a smartphone, so why do I need another device that essentially duplicates functionality of my phone? It is an honest argument, but I'll concede that I was wrong -- smartwatches rock. Well, to be more specific, Android Wear in particular kicks major ass. I love my Samsung Gear Live which I recently got.
When the smartwatch concept started to take off, I was dubious to say the least. I mean, I own a smartphone, so why do I need another device that essentially duplicates functionality of my phone? It is an honest argument, but I'll concede that I was wrong -- smartwatches rock. Well, to be more specific, Android Wear in particular kicks major ass. I love my Samsung Gear Live which I recently got.