
As the online world gets scarier by the day, security becomes a more discussed topic. This is a shame because, computer security should always be on the minds of users. Sadly, it takes something like the Heartbleed bug, the Target breach or a whistleblower like Edward Snowden to make people start caring. In other words, security is not more important today than it was prior to Heartbleed -- it is just finally being discussed.
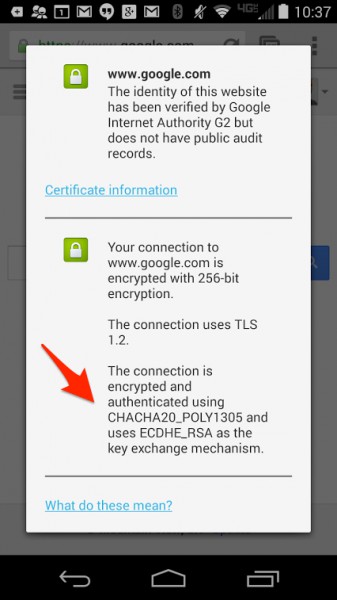
Say what you want about Google, but the company seemingly has security as an important focus. After all, it patched Heartbleed on its services with incredible speed. Today, Google announces that earlier this year, it improved HTTPS connections on Chrome for Android, making it dramatically faster and stronger.
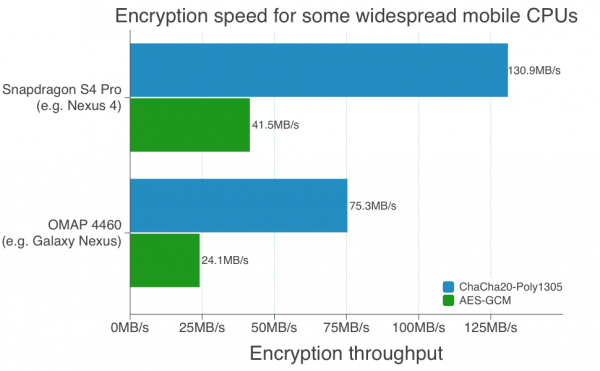
"Earlier this year, we deployed a new TLS cipher suite in Chrome that operates three times faster than AES-GCM on devices that don’t have AES hardware acceleration, including most Android phones, wearable devices such as Google Glass and older computers. This improves user experience, reducing latency and saving battery life by cutting down the amount of time spent encrypting and decrypting data", says Elie Bursztein, Anti-Abuse Research Lead, Google.
Bursztein further explains, "to make this happen, Adam Langley, Wan-Teh Chang, Ben Laurie and I began implementing new algorithms -- ChaCha 20 for symmetric encryption and Poly1305 for authentication -- in OpenSSL and NSS in March 2013. It was a complex effort that required implementing a new abstraction layer in OpenSSL in order to support the Authenticated Encryption with Associated Data (AEAD) encryption mode properly. AEAD enables encryption and authentication to happen concurrently, making it easier to use and optimize than older, commonly-used modes such as CBC. Moreover, recent attacks against RC4 and CBC also prompted us to make this change".
Google touts the following benefits:
-
 Better security: ChaCha20 is immune to padding-oracle attacks, such as the Lucky13, which affect CBC mode as used in TLS. By design, ChaCha20 is also immune to timing attacks.
Better security: ChaCha20 is immune to padding-oracle attacks, such as the Lucky13, which affect CBC mode as used in TLS. By design, ChaCha20 is also immune to timing attacks. -
Better performance: ChaCha20 and Poly1305 are very fast on mobile and wearable devices, as their designs are able to leverage common CPU instructions, including ARM vector instructions. Poly1305 also saves network bandwidth, since its output is only 16 bytes compared to HMAC-SHA1, which is 20 bytes. This represents a 16% reduction of the TLS network overhead incurred when using older ciphersuites such as RC4-SHA or AES-SHA.
Believe it or not, since February of this year, the majority of HTTPS connections on Chrome for Android have used the cipher suite. In fact, it has been so successful, that it will be baked into future Android versions. This is just another example of Google being on the forefront of computer security.
Do you now feel safer using Chrome on Android? Tell me in the comments.
Photo Credit: Darren Whittingham/Shutterstock

