
The slow drip of revelations about Flame have kept this piece of malware in the news for more than two weeks so it is worth reminding people that most antivirus programs now protect against Flame (ESET products detect it as Win32/Flamer.A). The coverage of Flame was boosted last week by a conveniently-timed assist from leaks that put Stuxnet back in the headlines.
Frankly, many antivirus experts were underwhelmed by reports that anonymous officials in the US. government were asserting that the industrial-sabotage malware known as Stuxnet was developed as part of attacks on Iran's industrial infractructure sanctioned by the President of the United States (a lot of us already assumed that was the case). There has also been a longstanding presumption of Israeli involvement in Stuxnet and so it was no surprise to hear "Stuxnet is our baby; Obama disclosed it for his reelection campaign" coming from Mossad agents. The third unsurprising revelation is that part of the Flame code is nearly identical to code found in Stuxnet.
Of course, that fact alone does not mean the same organization wrote both Stuxnet and Flame or that there were two teams who collaborated. All code can be used and abused by anyone who gets a copy. And that seems to be the part of the Flame/Stuxnet story that is being overlooked: Your taxpayer dollars are being used to develop malicious code that cannot be controlled or contained, and the effects of which cannot reliably be predicted.
This "gift to the bad guys" was a topic I discussed with TechTarget's Rob Westervelt and Jim Lewis of the Center for Strategic and International Studies on a recent podcast: Demystifying nation-state attacks and their impact. The short-term implication is that our government is putting malicious code into the wild where bad guys can copy and modify it for their own ends.
The long term implications are even worse. A large slice of the American economy is digitally driven and Internet-based. Malware undermines the trust we place in all things networked and digital. When our own government adds to the malware threat it adds to an erosion of trust that undermines the digital economy. That's why I think nation-state malware has a negative impact on GDP.
I expect some eager students of economics are already crunching the numbers to verify or refute this hypothesis. I do know for a fact that some economists are very interested in the relationship between trust and economic growth. For example, here two economists based in Paris, Yann Algan and Pierre Cahuc show that GDP per capita in 2000 would have been more than 100% greater in Africa and India if the level of inherited trust among the working age population had been the same as in Sweden by that time:
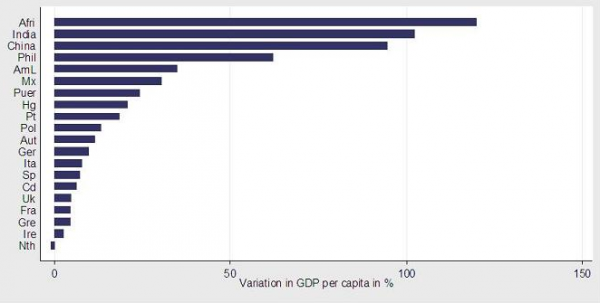
This graph comes from the article "Social attitudes and economic development: an epidemiological approach." The article is well worth reading, as are the documents the authors reference. As you read, consider to what extent your trust in LinkedIn was impacted by their recent security breach, or any of the many hundreds of other examples of security breaches in the last 12 months, a signficant percentage of which were aided and abetted by malware.
Malware erodes trust and in my opinion our goverment should not be making it or spreading it. But don't just take my word for it. Consider who else is warning about the dramatic cascading effects of weaponized malware: The White House's first cybersecurity coordinator, Howard Schmidt, former president and CEO of the international nonprofit Information Security Forum and chief information security officer at eBay and Microsoft. While antivirus researchers are prepared to keep up the good fight against malware, it would be a relief to hear that our government is now ready to think twice about adding to the problem.
Reprinted with permission.
Photo Credit: Bartlomiej K. Kwieciszewski/Shutterstock
A Certified Information System Security Professional since 1996, Stephen Cobb has more than 20 years’ experience helping companies, government agencies and consumers to manage their computer security and data privacy, notably in the area of emerging threats. Now based in San Diego, he works on the Research team at ESET in the role of security evangelist.


 Say, it must be vacation time. The folks from Redmond, Wash. will trek to Los Angeles for a mysterious June 18 event. It's the right month to soak up Southern California sun. Timing surely isn't coincidental -- a week following Apple's swaggering
Say, it must be vacation time. The folks from Redmond, Wash. will trek to Los Angeles for a mysterious June 18 event. It's the right month to soak up Southern California sun. Timing surely isn't coincidental -- a week following Apple's swaggering 

 Skype has just launched Skype
Skype has just launched Skype  It is a dark day for the employees of the world's most-recognized phone maker in Espoo, Finland. Stephen Elop, Nokia CEO, announced today that 10,000 positions will be made redundant by the end of 2013. In what is being called part of a strategy to rescale Nokia's operations after terrible losses over the past four quarters, offices in Finland, Germany and Canada will close. Also executives Niklas Savander, Mary McDowell, and Jerri DeVard will step down.
It is a dark day for the employees of the world's most-recognized phone maker in Espoo, Finland. Stephen Elop, Nokia CEO, announced today that 10,000 positions will be made redundant by the end of 2013. In what is being called part of a strategy to rescale Nokia's operations after terrible losses over the past four quarters, offices in Finland, Germany and Canada will close. Also executives Niklas Savander, Mary McDowell, and Jerri DeVard will step down. 

 Emptying your Recycle Bin and clearing away temporary files are a good first step in cleaning up your system, but there’s another type of hard drive clutter which is a little less obvious: duplicate files. These can consume a surprising amount of hard drive space, but fortunately tools like
Emptying your Recycle Bin and clearing away temporary files are a good first step in cleaning up your system, but there’s another type of hard drive clutter which is a little less obvious: duplicate files. These can consume a surprising amount of hard drive space, but fortunately tools like