By Scott M. Fulton, III, Betanews
One of the extraordinary truths about the Internet as a mechanism is that the databases that enable every IP address to be resolved, are maintained and published by a very small number of organizations acting as a cooperative. The health of the entire network depends on these groups' vigilance. One of these groups is Autonomica AB, a division of the Swedish ISP Netnod. It operates the "I" root server, which in recent weeks has been the apparent victim of a kind of spoofing attack that's been harmless thus far, but could conceivably demonstrate the capability of one rogue element to pollute the entire Internet.
Thanks to the current state of affairs, some are now suspecting a China-based culprit. But as we all know with the Internet, just because a malicious server resides in one country doesn't mean its malicious operator works there as well.
As first reported yesterday by Ars Technica's Iljitsch van Beijnum, engineers for the world's root servers reported on their public mailing list that certain requests sent to the "I" server for authoritative information were being resolved in a peculiar manner. Normally a root name server responds with the address of authoritative servers for a top-level domain; and thanks to a technique called anycasting, the server doing the responding may not be the same one each time. But at least one such server somewhere was occasionally responding to specific requests to resolve addresses that have the text facebook, twitter, or youtube in them (for example, www.facebook.com or whattheheckcouldthismeanforfacebook.co.uk) with apparently random IP addresses that served no function at all, malicious or otherwise. Also, requests for information on specific IP address ranges were met with similarly spoofed responses, intermittently.
On Wednesday, a root server network operator in Chile reported being told by a local ISP that one of the "I" server nodes, i.root-servers.net, was responding to requests to resolve Facebook addresses with a random IP address. When the incidents occurred, the traceroute for the "I" server runs through China. Other operators familiar with China's track record for tinkering with IP addresses were amazed, including one Dutch operator who responded, "Wow! This is stunning. I knew that China messed with DNS internally, but not that it leaked to the outside world."
The symptom of DNS requests for records matching a certain text pattern being met with inaccurate data, follows a trend that researchers have noticed before -- which is why China emerges as a leading suspect. In December 2007, a trio of NYU researchers published the findings of research they had conducted into the veracity of DNS requests from Chinese name servers. In their paper, "The Great DNS Wall of China" (PDF available here), they demonstrated how China-based DNS servers responded to DNS requests for domains whose names consisted of random alphanumeric characters (they couldn't possibly exist), but whose subdomains contained certain "red-flag" phrases such as falungong, voanews, and minghui (which refers to the Buddhist Falun Dafa practice). The responses, which should have been confusing as well, instead appeared to be authoritative.
In a first round of tests in which Chinese servers were asked to resolve requests for 841 domain names for which five US-based servers were in complete agreement, the trio wrote, "We observed that almost all of the Chinese DNS servers returned tampered responses for 383-393 domains and that the number of distinct IPs returned for these responses was extremely low when compared to the uniqueness of the correct responses. In fact, 366 bad domains shared eight IP addresses."
Then the group applied the nonsense domains, which the US servers couldn't possibly resolve. "We found that, as expected, the canonical US servers returned a 'domain does not exist' for all of the nonsense domains. The Chinese servers exhibited different behavior. For both the domains with a control subdomain (i.e., www) and domains that had a keyword embedded as a subdomain, the majority of the servers returned a 'domain does not exist.' The nonsense domains with the censored domains embedded as the subdomain triggered the same type result as the previous experiment, returning the set of eight IP addresses."
A representative from China's network information center CNNIC denied his department's involvement in any spoofing activity, to the operators' mailing list.
On July 1, 2010, DNSSEC will be deployed at the root server level, enabling encrypted and secure communication there for the first time. Theoretically, this would disable the type of spoofing exhibited here.
As the Dutch network operator commented, "Given the nature of why this is happening, this is one of the first use cases I see for DNSSEC that actually is worth the administrative overhead. Preventing Kaminsky spoofing, which appears not to be happening anyhow, is not that exciting, and may not be worth the effort. But preventing nation states from globally changing DNS traffic (even if only by accident), far beyond their shores, might be a great idea."
That prompted a Dutch security engineer to respond with a scenario whereby a hypothetical name server decides not to employ DNSSEC after all. In his scenario, that hypothetical server could respond to requests that mandate DNSSEC be turned on, with signed connections to false copies of root zone information. "If I can control all the roots, then DNSSEC buys you just a false sense of security," he wrote. "Control the roots, control the data."
Copyright Betanews, Inc. 2010









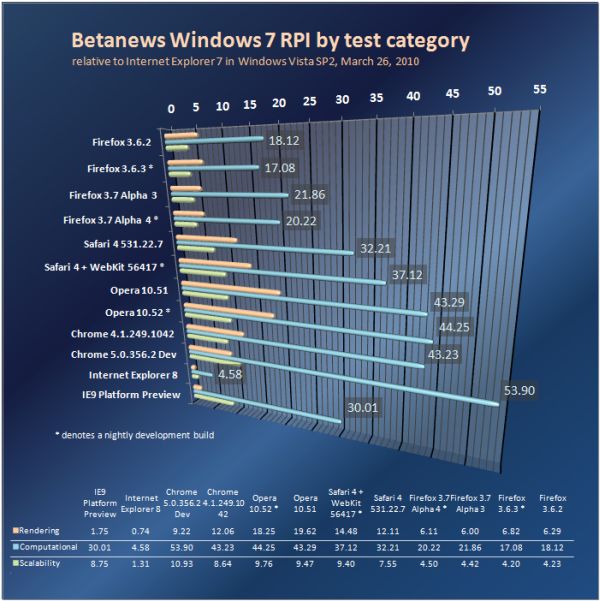
 In the latest check of progress in the development of the major Web browsers for Windows, the brand that helped Betanews launch its regular browser performance tests appears to be making a comeback effort: With each new daily build, the WebKit browser engine -- running in Apple's Safari 4.0.5 chassis -- gains computational speed that it was sorely lacking.
In the latest check of progress in the development of the major Web browsers for Windows, the brand that helped Betanews launch its regular browser performance tests appears to be making a comeback effort: With each new daily build, the WebKit browser engine -- running in Apple's Safari 4.0.5 chassis -- gains computational speed that it was sorely lacking.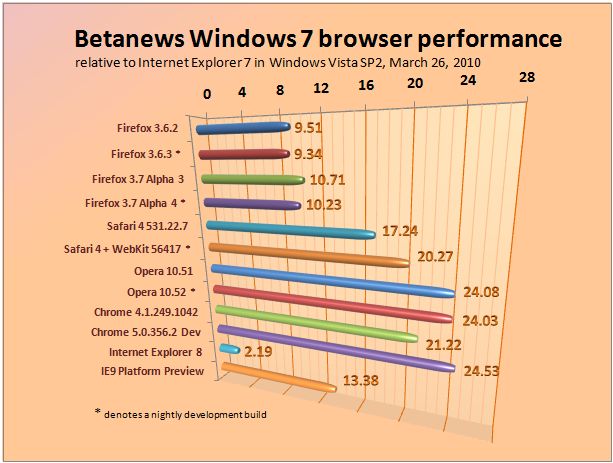
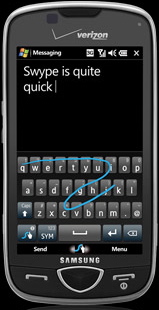 This week, Nuance announced its new method of text entry called T9 Trace, which is pretty much exactly the same as Swype. Both Nuance and Swype market their products directly to OEMs rather than fiddle with the consumer app space, so the name of the game for them is getting as many manufacturers to pick up their technology, and establishing ubiquity.
This week, Nuance announced its new method of text entry called T9 Trace, which is pretty much exactly the same as Swype. Both Nuance and Swype market their products directly to OEMs rather than fiddle with the consumer app space, so the name of the game for them is getting as many manufacturers to pick up their technology, and establishing ubiquity.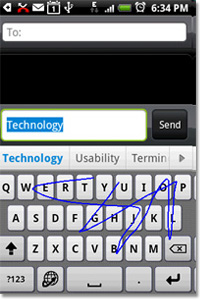 In other words, manufacturers who already license T9 will be able to get a package licensing deal with Nuance for Trace and whatever other technologies they want.
In other words, manufacturers who already license T9 will be able to get a package licensing deal with Nuance for Trace and whatever other technologies they want.