By Scott M. Fulton, III, Betanews
 A blog post Tuesday by Sophos senior security engineer Chester Wisniewski stated that recent Sophos tests revealed that User Account Control -- the part of Windows that prompts the user for permission before granting elevated privileges -- was ineffective in stopping common samples of malware from running, in a Windows 7-based system without virus protection.
A blog post Tuesday by Sophos senior security engineer Chester Wisniewski stated that recent Sophos tests revealed that User Account Control -- the part of Windows that prompts the user for permission before granting elevated privileges -- was ineffective in stopping common samples of malware from running, in a Windows 7-based system without virus protection.
Whereas two of the ten chosen malware samples for the test would not run in Win7 without UAC turned on at all, only one more sample (a low-prevalence worm code-named W32/Autorun-ATK) was thwarted by UAC. The other seven ran as though they were being blocked only by a stack of dominoes.
Those items that ran unimpeded were: Troj/FakeAV-AFY and Troj/FakeAV-AFX, two low-prevalence Trojans that pretend to be a free anti-virus test; Mal/EncPk-KY and Mal/EncPk-KP, two garden-variety spam viruses; Troj/Agent-LIW, a low-prevalence Trojan that adjusts the behavior of Internet Explorer; Troj/Zbot-JN, a variation of the Trojan that attempts to steal online banking login information by first masquerading as an anonymous e-mail request for a date; and W32/Autorun-ATC, a garden-variety worm that changes the startup script.
"User Account Control did block one sample; however, its failure to block anything else just reinforces my warning prior to the Windows 7 launch that UAC's default configuration is not effective at protecting a PC from modern malware," Wisniewski wrote.
That default configuration is a new setting for Windows 7, that's one level down (and one level less annoying for some users) than Vista's default. During the testing process earlier this year, Windows 7 generated considerable controversy for effectively enabling some applications to generate a kind of "privilege self-elevation privilege" for themselves, which some saw as a vulnerability gift-wrapped for anyone wanting to go exploiting it. Others complained about a more sweeping potential problem: that the whole point of generating the message in the first place (stopping privilege elevation) is forfeited if developers leave a back door wide open.
As Wisniewski told Betanews this afternoon, his intention was not to prove UAC pointless in and of itself, but to suggest that Windows 7 may be vulnerable right out of the box unless and until users do something above and beyond the default.
"This was a quick test to determine if the efficacy of restricting administrative rights through the use of UAC alone will protect against malware infecting a computer running Windows 7," Wisniewski told us. "I did not test how it would have behaved if UAC was dialed up, or perhaps run in what people are calling 'Vista mode.'"
But if anti-virus is the solution to the problem (of course, Sophos is an anti-virus software maker), then what good is UAC at all, even if it's dialed up? Is Chet suggesting the whole thing is pointless anyway?
"I am performing some follow-up testing, although as is the case with malicious software, it does take a bit of time to safely perform these tests. With the data I have at the moment, I am not making recommendations as to what you do with UAC," he responded, "merely warning people that it does not protect a machine effectively against malware. I think Microsoft acknowledges this with their efforts on Microsoft Security Essentials and Forefront." But isn't UAC generally effective against malicious applications that seek elevated privilege levels, even if they're not among the most dangerous viruses cited by Sophos?
"We did not select specific malicious or difficult samples, merely the most recent ten at the time. Most were 'Fake AV' even if the sample names did not indicate that. We have generic detection for malicious packers and other nastiness that proactively finds many samples...With proper anti-malware protection, Windows 7 is far safer," acknowledged Sophos' security engineer.
"One benefit that UAC could have provided," he continued, "is an additional layer of protection that would help in the event that your anti-virus has failed to detect a new sample. It does not appear from my results that this is the case."
Copyright Betanews, Inc. 2009









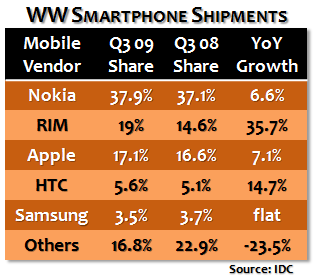
 It's a lesson that RIM would do well to learn, because at this critical inflection point in its history, a stay-the-course mentality could doom RIM to a Nokia-like fate.
It's a lesson that RIM would do well to learn, because at this critical inflection point in its history, a stay-the-course mentality could doom RIM to a Nokia-like fate.