
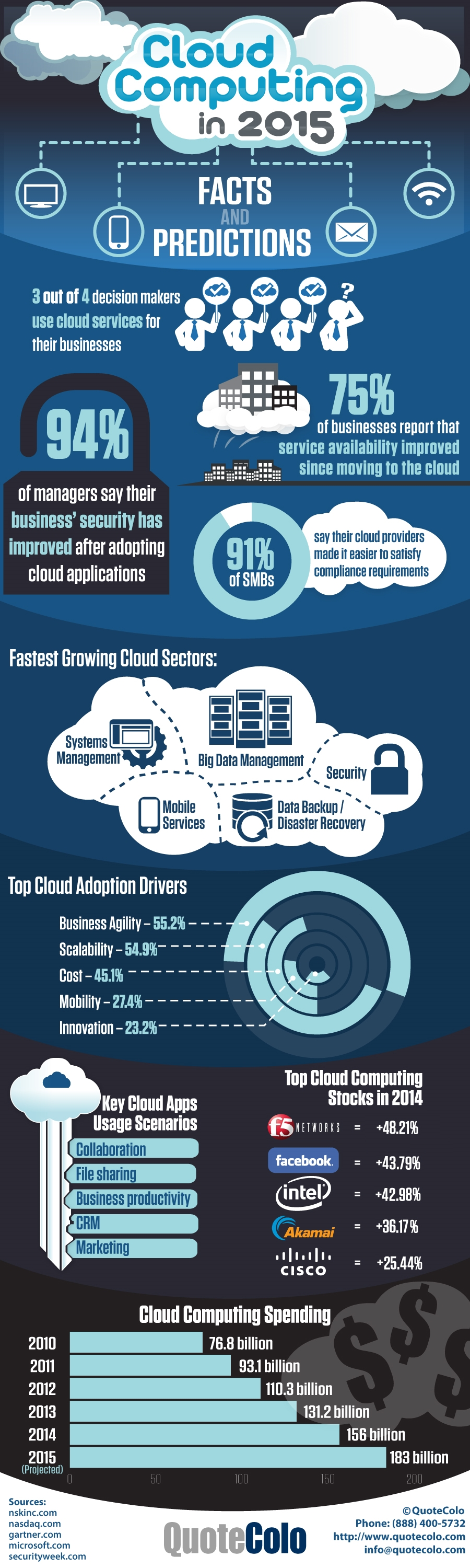
One of the most interesting aspects of the "Cloud Computing in 2015" infographic produced by QuoteColo is this: 94 percent of business managers state that security has improved after adopting cloud applications.
While reading this stat on an infographic is comforting, we want to explore the statistic more to discover why and how cloud applications have made businesses more secure. But before we can get into why cloud applications have made businesses more secure, we need to talk about the false illusion of porous cloud security.
The illusion of service provider and on-premise IT environment security
When most people think about the cloud, security is not the term that comes to mind. This gut feeling is wrong. In a study conducted by Alert Logic, titled The State of Cloud Security Report, the specific finding is "anything that can be possibly accessed from outside -- whether enterprise or cloud -- has equal chances of being attacked, because attacks are opportunistic in nature".
The report found web application attacks targeted and successfully compromised service provider environments (53 percent of all organizations) and 44 percent of on-prem IT environments. More to the point, on-prem IT environments suffered 61.4 attacks per year as opposed to 27.8 for service provider environments. This clearly illustrates that non-cloud based IT environments are highly vulnerable to security threats.
Many people believe that the more control a company or service provider has over its servers, the more secure that environment is. This simply isn’t true.
How cloud applications strengthen IT environment security
The major misconception concerning IT security is the location of your data. With cloud based applications, data is stored on servers, hardware and systems you don’t have direct control over or ownership of. While this may make some business owners think that their data is less secure, it’s the other way around: because your data is stored offsite in servers and cloud applications you don’t own, it is more secure.
Here’s why:
- Offsite cloud applications typically require more stringent firewalls, access credentials and security protocols than onsite stored data. With onsite stored data, security protocols tend to wane because they nest behind a local firewall onsite. On the other hand, offsite cloud applications must adhere to much more stringent security protocols, to make sure business owners are comfortable storing materials offsite and to make sure that access to those materials remains muted from the outside world.
- Offsite cloud applications are stored within the walls of a 24/7/365 physically secured data center facility. All too often companies make the mistake of thinking their data is secure because it is stored on site, when they should really be noticing that onsite data storage leads to a much higher risk for the data to leave the building due to negligent employees. Cloud application data, which is stored in a secured data center facility, lessens this possibility by securely managing all physical bodies allowed to physically access hardware and virtual environments wherein data is stored.
- Utilizing a cloud application means building a threat assessment model. A good cloud security threat assessment model will work to identify possible leaks within business cloud applications, and constantly work to break those security measures, in an effort to make them stronger and stronger. While a few of the onsite IT environments might take this step, most of them won’t.
It is clear that security in the cloud has nothing to do with location. It has everything to do with access protocols, testable firewalls and physical access to data. While onsite IT environments might give the illusion of an increased security, cloud apps are definitely the way to go.
Bob Spiegal is CEO of Quotecolo, you can follow him on Twitter @quotecolo
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.

