Malware analysis normally starts with logging the executables launched on a system: opening this document, launches that application, fires up some scripting tool, which downloads and runs the actual threat (or something like that).
You could use something like Process Monitor to record what happens, but analyzing the logs will take time, and the malware might delete key files before you can inspect them.
NoVirusThanks PE Capture simplifies the process by capturing and save PE executable images -- EXEs, drivers, DLLs -- as they’re loaded, making them supremely easy to analyze later.
The program is portable, no full installation required. Unzip it, launch the 32 or 64-bit EXE depending on your system, and it temporarily installs the kernel driver which carries out the captures.
Just watch the display and, as processes run in the background, you’ll see the relevant DLL or EXE logged, along with its execution time.
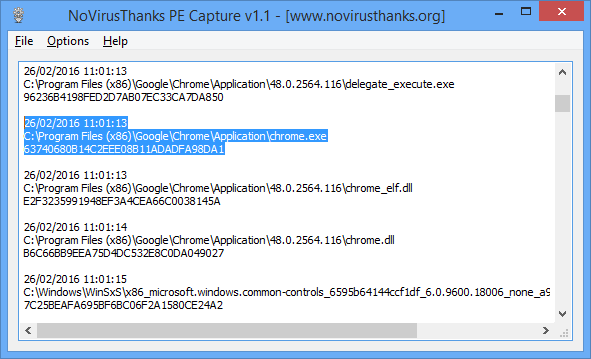
Test the system further by launching some other application of your own. Google Chrome is a good choice as it fires up several EXEs and DLLs.
Browse to your \pe_capture_portable\PORTABLE\Intercepted\xx-xx-2016 folder at any time, and you’ll see all the captured images, renamed to their MD5 file hashes.
Image capture and execution logging can be toggled on or off at any time by selecting that item on the Options menu.
When you’re done, the text log displays the date and time each file was loaded, along with its MD5 hash.
If you’re interested in a particular file, look for that MD5 hash in the Intercepted folder.
But if you’re more generally curious about what’s just been launched, then point your antivirus tool of choice at the Intercepted folder and see what it discovers.
NoVirusThanks PE Capture is a free tool for Windows XP and later.

