While there used to be a wide range of specialist rootkit detectors available, most of the projects have been abandoned in recent years, with even apps like Bitdefender’s Rootkit Remover quietly forgotten.
But if you need some extra help in detecting stealthy malware, don’t give up -- Resplendence Software’s SanityCheck is still alive, and last week added support for Windows 10.
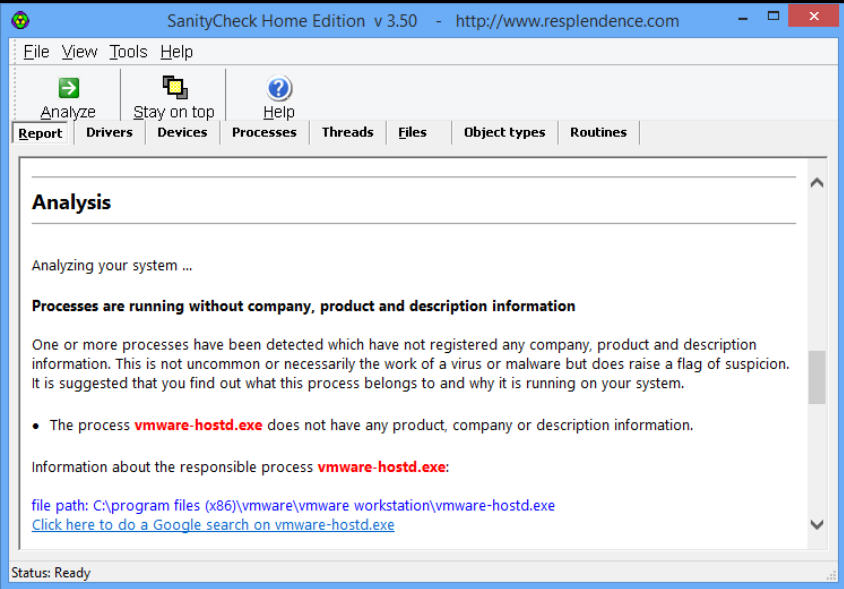
The program is definitely one of the simpler detectors around. There’s no real-time protection, no massive signature database, no removal afterwards: it just follows some general rules to detect processes which might be suspicious.
Still, this does at least keep the program usable by anyone (all you have to do is run it, click Analyze, then scroll down and read the report), and the official list of scanned objects looks good to us:
- Hidden processes
- Processes with spoofed names
- Processes attempting to appear as standard Windows processes
- Processes with obviously deceptive names
- Processes without product, company and description information
- Valid signatures in processes and kernel modules
- Intercepted system services and the modules responsible
- Intercepted kernel routines and the modules responsible
- Intercepted kernel object callout routines and the modules responsible
- Drivers with intercepted dispatch entry points
- Hidden drivers
- Hidden files
SanityCheck isn’t a program you’ll use every day, but if you think you’re infected by something and your regular antivirus tool hasn’t raised an alert, it just might point you towards the problem.
SanityCheck is a free-for-personal-use tool for Windows 2000 (yes, really) and later, both 32 and 64-bit editions.

