
There we are: the last Patch Tuesday of 2015. It turns out to be about average, with maybe a bit more severity in the bulletins than usually. We have eight critical bulletins in the total 12, including one that fixes a 0-day vulnerability, currently in use by attackers to escalate privileges in Windows. 0-days used to be very rare occasions, but this year they have become almost mainstream.
After all the year started off with a string of 0-days in Adobe Flash and since then we have seen almost every month a patch for a vulnerability that is already under attack. Definitely a sign of the increasing technical capabilities that attackers are wielding and a reminder that IT Managers should not only patch their systems promptly, but also look for additional robustness.
Your list of things to look at in 2016 should include investigation of minimal software installs with the least features enabled, plus an additional piece software such as EMET that enhances robustness.
In total we had 135 bulletins from Microsoft in 2015, which is a significant increase from the average of the last years. New products by Microsoft only explain a small part of this increase, for example the new Edge browser only added five bulletins of its own this year.
The majority of the increase is due to new parts of the Windows ecosystem that are being investigated for the first time, a tendency that shows how much more important computer security has become over the years.
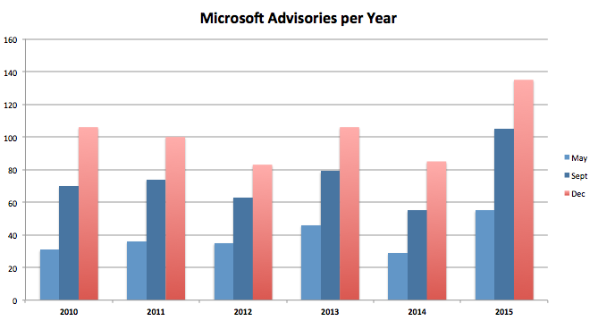
Let’s take a closer look at this month’s patches.
MS15-135 addresses a 0-day vulnerability in the Windows kernel. There is no further information about how widely spread the vulnerability and its exploit are, but it is worth a top spot in our priority list.
Browsers are often used in current attack scenarios, such as drive-by downloads or spear phishing. You need to keep them as up-to-date as possible. MS15-124 for Internet Explorer (IE), MS15-125 for Edge and MS15-126 for the JavaScript libraries in Vista and Windows Server 2008 address 30 issues, many of them critical leading to remote code election (RCE). Edge has "only" 15 issues, with 11 duplicates from IE and four issues native to Edge itself.
MS115-131 for Microsoft Office is next on our list. It is rated critical by Microsoft, which is rare for Office bulletins and means that a vector exists to abuse the vulnerability with no user interaction. CVE-2015-6172 is a critical vulnerability in Outlook that is triggered by a maliciously formatted e-mail message.
There is no reasonable workaround: Microsoft suggests turning off the preview pane - the digital equivalent of "Just don’t do it", so patch this vulnerability as soon as possible. CVE-2015-6124 is being exploited in the wild by attackers.
Next is a server side vulnerability in Microsoft DNS server, which is quite a rare find. MS15-127 replaces MS12-017 from over 3 years ago. Attackers that exploit MS15-127 in Microsoft’s DNS server would gain control over the server and execute code in the system context.
The attack is remote and does not require authentication, and no workarounds are available. Bring your Microsoft DNS servers up to date as soon as possible, with the required testing and soak time for such a fundamental service.
The next critical vulnerability is in the Windows Graphics system (MS15-128), which has font handling problem. It replaces MS15-097 from September, which replaced MS15-077 from July, so they are quite common occurrences. Attack vectors are very wide, as web browsing, e-mail, documents and rich media through Silverlight can all be used for an attack.
The remaining critical vulnerabilities are in Silverlight (MS15-129) and Uniscribe (MS15-130). Address them together with the important vulnerabilities MS15-132, MS15-133 andMS15-134.
In addition to the Microsoft updates we also have a new version of Flash from Adobe. APSB15-32 addresses a record number of 78 vulnerabilities. All but three of the vulnerabilities could be used by an attacker to gain code execution running under the user in the browser.
From there, a second vulnerability would have to be used to become system on the machine (look at MS15-135 for an example), but then the attacker would have full control. Flash-based attacks have been a favorite for attackers for the year with many exploit kits providing very up-to-date exploits -- include this in your high priority items.
 Wolfgang Kandek, CTO, Qualys.
Wolfgang Kandek, CTO, Qualys.
Image Credit: Manczurov / Shutterstock

