Run a Windows program and it’ll often try to access functions or data in a Dynamic Link Library (a DLL file). If the program has provided a copy of the DLL then Windows will load that, otherwise it’ll search various folders on your system to find a copy.
Sounds great, in theory, but there can be problems. If you have multiple copies of a DLL scattered around your system, applications won’t always get the versions they expect. And if malware copies a DLL to a preferential point in the Windows search order – so-called “DLL hijacking” – then you could be running malicious code whenever it’s requested.
DLL Hijack Detect is a simple command line tool which can help you discover whether this might be an issue on your own PC.
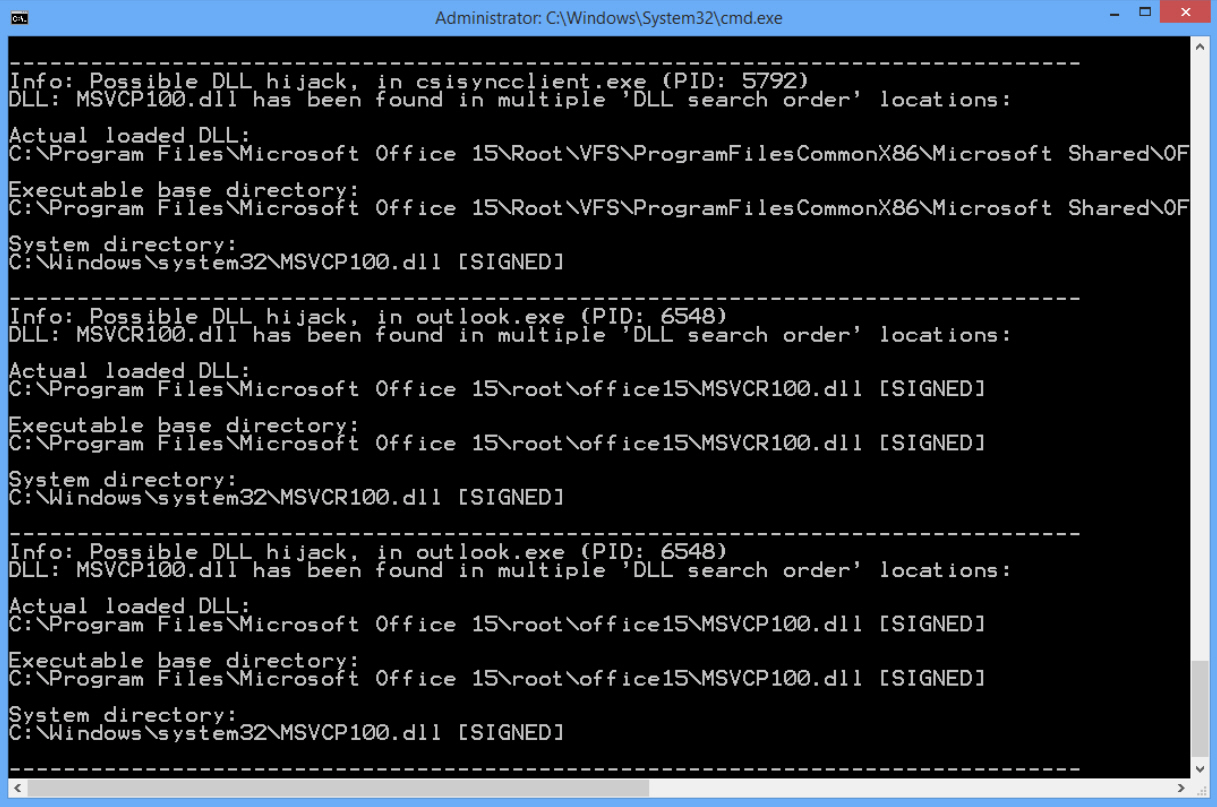
To use it, launch any application you think might be infected, then run DLL Hijack Detect from an elevated command prompt. It scans running processes, checks their loaded DLLs and reports on any which appear more than once in the search order.
Don’t panic if you see a few items listed, this is entirely normal and doesn’t necessarily mean you have any security issues. For example, we were told that Outlook.exe had loaded a copy of MSVCP100.dll from a subfolder of C:\Program Files\Microsoft Office 15\root, and there was also a copy in C:\Windows\System32. But these were the locations we’d expect, and both DLLs were signed, so it’s unlikely anything dubious was going on.
If the DLLs are unsigned, maybe saved in some unexpected locations, perhaps there are several copies around, you’re not sure of their purpose, and they’re being used in an interesting application (an obvious target like a browser, anything which has been unstable lately), then you might want to investigate further.
DLL Hijack Detect can’t provide any conclusive verdict, but it does make it a little easier for expert users to identify some DLL issues, and that’s more than enough to justify the 15KB download. Go grab a copy for your security toolkit.

