The "pay or lose your files" concept of ransomware seems to have taken off with hackers and crime syndicates, becoming the modern cyber equivalent of the mob shakedown. Sort of like paying "protection money".
Now a new ransomware variant has been spotted in the wild, spreading via email, just as previous ones had. The latest is being referred to by the catchy name of Trojan.DownLoad3.35539, and appears in a message as a ZIP file with hopes that unsuspecting recipients will launch it.
Russian security firm Dr. Web reports that "The archive contains an SCR file -- by default, the .scr extension is utilized for Windows screen savers. These files are executable. If the archived file is launched, Trojan.DownLoad3.35539 extracts an RTF document from its body, saves it onto the hard drive and displays it on the screen".
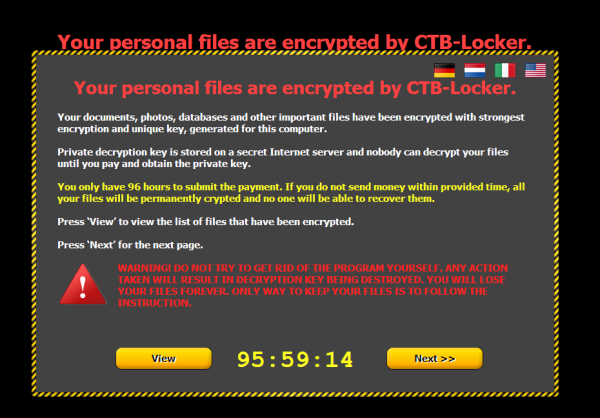
When this occurs the file downloads the encryption program from the criminal's server. This is then decompressed and executed, locking up the user's personal files. It then displays the message seen above and demands payment from a person in order to get back what is theirs. The money must be coughed up within 96 hours, and a helpful NASA-like countdown clock ticks the moments until doom.
The amount isn't listed, but users are instructed to visit a site which resides on the TOR network if they wish to pay the cash. "Trojan.Encoder.686 has been compiled using TOR and OpenSSL libraries and relies heavily on their encryption routines. While encrypting data, the ransomware makes use of CryptoAPI to generate random data as well as elliptic curve cryptography which for now makes it impossible to recover the affected data", claims Dr. Web.
This is perhaps a good time to once again preach about not opening suspicious attachments in email, even those from people you know. Sadly, this wouldn't be a problem if there weren't enough willing victims out there.

