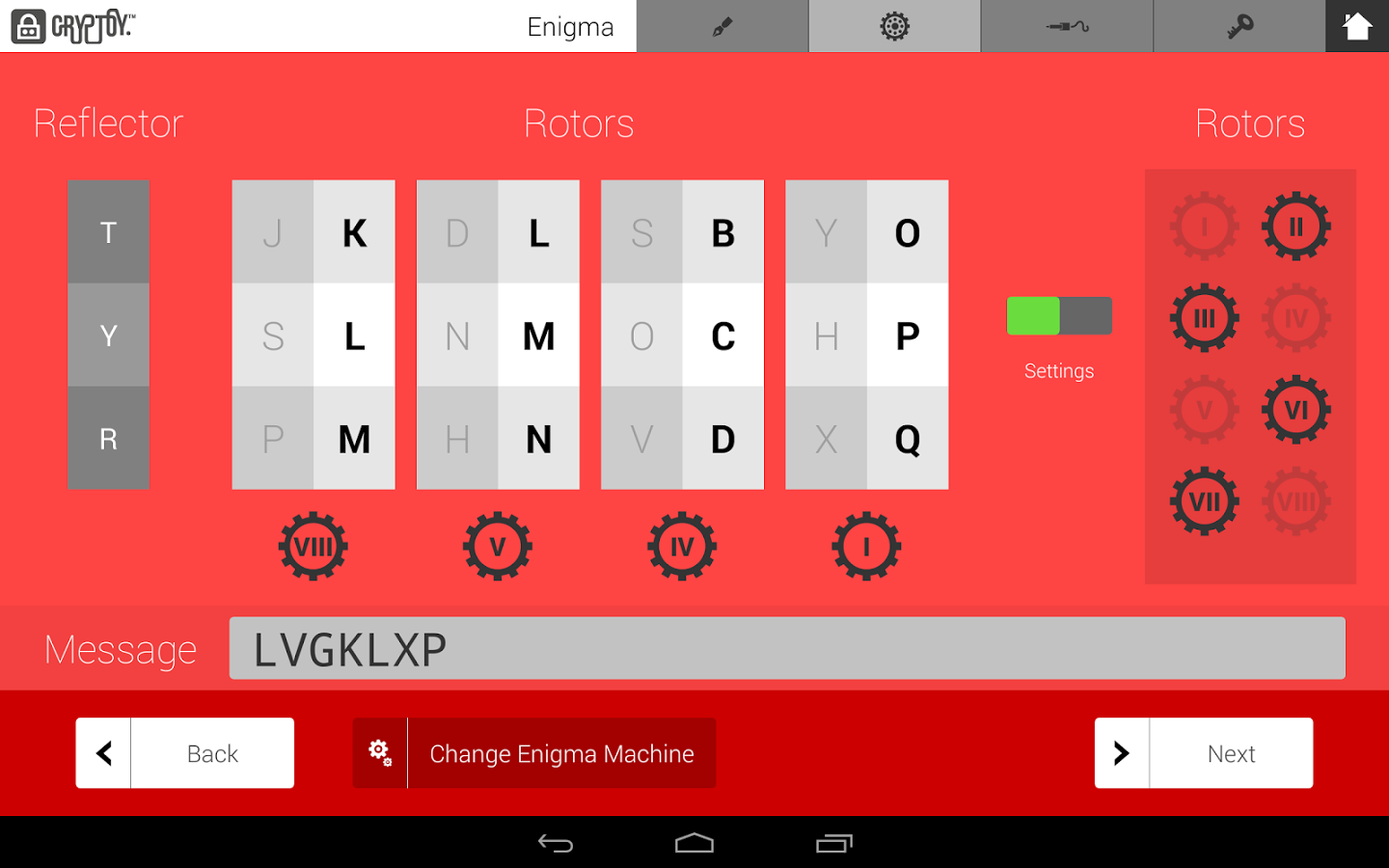
The UK’s history of cryptography is fascinating, with famous cryptanalysts like Alan Turing, Dillwyn Knox, and W. T. Tutte deciphering different code machines used in World War I and II.
To celebrate the achievements of the past and reinvigorate students on cryptography, the GCHQ (Government Communications Headquarters) has released a code-breaking app on Android, named Cryptoy. An iOS version is set to see a 2015 release.
Cryptoy currently focused on four methods of encryption: Shift, Substitution, Vigenère and Enigma. The app makes it especially hard at higher levels, testing students who have the ability to crack code.
The GCHQ is interested in finding the next batch of code-breakers for the future. It is unclear how the GCHQ will get in contact with the potential candidates, or how the GCHQ will be able to identify actual codebreakers from cheaters.
This is not the first time the GCHQ has used public routes to employ new code-breakers, the Daily Telegraph ran a cryptic crossword and those who solved it received a chance to work at the GCHQ.
Encryption has moved from a wartime function designed to hide messages, to a way for Internet services to provide security against surveillance. This has blackened the GCHQ’s reputation when it comes to codebreaking, and now the next generation will most likely be cracking Facebook or Apple code.
New encryption techniques are on the rise, as more people worry about who is reading their private messages. Apple and Google recently announced new encryption on mobile devices, set to stop the FBI from accessing the devices without a warrant.
Terrorist organizations still use some encryption techniques when messaging, but some have been caught chatting on Facebook about potential attacks. The attack on UK soldier Lee Rigby was reportedly planned on Facebook a year beforehand the incident.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.

