Window Sysinternals has announced a brand new tool, Sysmon, a Windows service and driver which logs process creations, network connections, and changes to a file’s creation time.
The service is designed to help users identify malware, but can also be helpful when troubleshooting, or whenever you need to know more about what’s happening on a PC.
Sysmon has no GUI. To install the service, enter Sysmon -i at an elevated command prompt, or Sysmon -i -n to monitor network connections as well (run Sysmon with no switches and it displays all your options).
If everything has worked correctly, the Sysinternals EULA will be displayed. Agree to it, then reboot to run your first test.
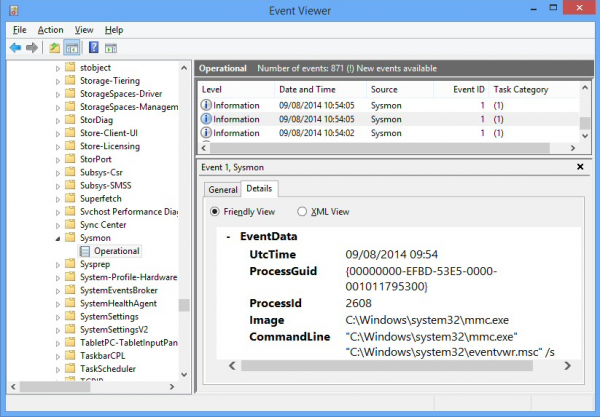
Once Windows has started again, launch the Event Viewer (Eventvwr.msc), and browse to the Windows System log on XP, Applications and Services Logs\Microsoft\Windows\Sysmon\Operational for Vista and later.
You should now see multiple events listing Sysmon as a source, along with their date and time, giving you much more detail about what happened during your system boot.
Events with an ID of 1 list a process creation, including the time of launch, Process ID and GUID, file name, command line, user, hash, the parent process and more.
Events with an ID of 2 highlight an attempt to change a file creation date. The report lists the responsible process, the file it’s trying to change, the previous and new dates.
Events with an ID of 3 record network connections, again listing the source process (ID/ GUID/ file name/ user), source and destination IP addresses, host names, ports and port names. (For some reason the host names weren’t resolved in our first test, but this worked properly after we rebooted.)
Basic log management tasks can be carried out with the regular Event Viewer tools. You’re able to filter the log, display just the events you need, search for something important, disable logging when it’s no longer needed, save the events to a file, and more: right-click Sysmon\Operational to see what’s available.
You can also change Sysmon to use its default configuration (no network connection logging) by running Sysmon -c – , or uninstall it entirely with Sysmon -u. The service and driver are removed immediately, and there’s no reboot required.
Sysmon is relatively limited in what it can monitor, but does have several advantages. It survives reboots, is launched very early in the boot process (handy if you’re looking to detect stealthy malware), and is invisible to regular users. Recording its findings as events also ensures you’ve plenty of ways to view and filter them, and overall it looks like another handy Sysinternals tool for power users.

