 NirSoft has announced the public availability of DNSQuerySniffer, a tiny (130KB, including a Help file) network sniffer which detects and displays your DNS traffic.
NirSoft has announced the public availability of DNSQuerySniffer, a tiny (130KB, including a Help file) network sniffer which detects and displays your DNS traffic.
If you think this sounds just a little technical, then you’re right, but the program does have some interesting applications. Malware will often use DNS traffic to communicate with its operators, for instance, and so taking a closer look at your own system may reveal the signs of an infection (a large number of failed lookups to domains you don’t recognize, say).
And more generally, DNSQuerySniffer helps to reveal which of your applications is trying to go online, and maybe what they’re trying to do.
The data capture itself can be done via WinPcap and Microsoft Network Monitor. But if you’d rather not install anything else, the program also supports Raw Sockets capture, and this may produce acceptable results (the documentation provided with DNSQuerySniffer explains more).
Any queries intercepted are displayed in full, with all the details you’d expect: Host Name, Port Number, Query ID, Request Type, Request Time, Response Time, Duration, Response Code, Records Count, and the returned records.
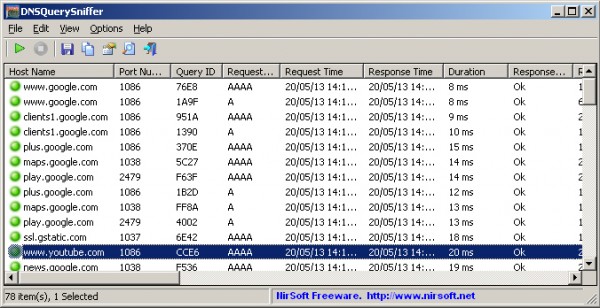
All of this data is displayed in a sortable table, and can be exported as a report in TXT, CSV, HTML and more.
And as usual with NirSoft tools, while it’s not something you’ll use every day, DNSQuerySniffer is still a welcome complement to the more regular TCP/IP connection monitors, and you should probably grab a copy for your networking and security toolkit.
Photo Credit: Yuriy Boyko/Shutterstock

