Security company Kaspersky Lab on Thursday announced it had discovered a malware called Gauss which ran from September 2011 to July 2012, and was similar in design to the notorious Flame worm. The company believes Gauss to have been another state-sponsored cyberweapon.
Kaspersky said Gauss was discovered because of the increased efforts to identify and halt international cyber-weapons in the wake of Flame, Stuxnet, Duqu, and other military-grade security threats.
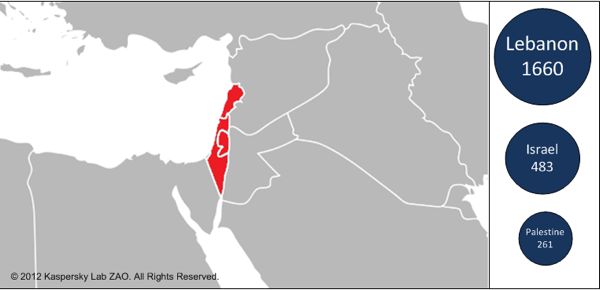
Gauss, according to the security company, was designed to steal sensitive information such as browser passwords, online banking account credentials, cookies, and local machine configurations/settings, and it infected approximately 2,500 machines, with Lebanon being the major target. Flame infected only about 700 machines.
"Functionally, Gauss is designed to collect as much information about infected systems as possible, as well as to steal credentials for various banking systems and social network, email and IM accounts. The Gauss code includes commands to intercept data required to work with several Lebanese banks - for instance, Bank of Beirut, Byblos Bank, and Fransabank," says the company's documentation of the malware.
"Code references and encryption subroutines, together with the Command and Control infrastructure make us believe Gauss was created by the same 'factory' which produced Flame. This indicates it is most likely a nation-state sponsored operation," the company said.
Kaspersky takes an aggressive position on international cyberwarfare, and warns that there is currently a global cyber arms race being built.
With this in mind, the company points out the major victims of the two similarly-crafted malwares were very different: Flame appeared to have targeted Iran, while Gauss appeared to have targeted Lebanon.
The command and control server IPs for Gauss were located in India, Portugal, and The United States, and the domains related to the malware were hosted alternately in India and Portugal as well.

