 This morning when I logged into LinkedIn I was greeted with several front page references to the reported hacking of the site, and instructions for changing my password, which I did immediately. This is a good time to change all of your social media passwords, making sure you create a fresh password that is hard to guess and unique to each site. It is not unusual for malicious parties who grab a bunch of passwords from one site to try those same passwords on other sites.
This morning when I logged into LinkedIn I was greeted with several front page references to the reported hacking of the site, and instructions for changing my password, which I did immediately. This is a good time to change all of your social media passwords, making sure you create a fresh password that is hard to guess and unique to each site. It is not unusual for malicious parties who grab a bunch of passwords from one site to try those same passwords on other sites.
Over 6.5 million account passwords showed up on a Russian forum in SHA-1 (hashed) format to prove that the hackers had indeed succeeded in penetrating LinkedIn. There is a good chance that if the hacker(s) achieved access to LinkedIn passwords then they also know the corresponding LinkedIn usernames, i.e. the matching email address of the account owner.
The difference with this hack, as opposed to many others, is that people put their real information about themselves -- their professional information -- on the site, not just what party they plan on attending, or which games they are playing, which you might see on other networks like Facebook. Furthermore, every time one of your LinkedIn contacts updates their profile, you get updates from LinkedIn showing what’s happening. This has the aggregate effect of a form of peer review on what you post about yourself, knowing that it is exposed to those business or career contacts that have a direct impact on your life. This causes people to tend toward being very accurate and honest on their LinkedIn profile. In other words, mess with somebody’s professional profile on LinkedIn, and you’re messing with their life, and their contacts know about it.
A broader question is how to assess the aggregate value of this level of business intelligence about an individual, let alone a whole business sector? This is the kind of information that advertisers and bad actors alike drool over. If, for example, you determined from LinkedIn that a competitor was losing staff at a rapid pace, it might affect a merger/acquisition negotiation, potentially swinging the value of the deal significantly. Also, since LinkedIn can be used as a sort of timeline of a user's real history, there are deep stacks of historic business intelligence that can be garnered.
It all adds up to a very bad day for LinkedIn, and we hope they take very proactive steps to assure users and protect data going forward. In the meantime, besides changing your password, it's a good idea to review your user settings and try to understand/limit/narrow access to your key information to those with whom you intend to share. In this way you can help prevent unintended data sprawl, also meaning other user accounts which might become compromised won't have as much of a direct effect on your personal information.
Several people have notified us that they received emails today asking them to confirm their LinkedIn email addresses and we have determined that these are scams. We are investigating the exact details but in the meantime please do not click on links in email to change or verify account information, at LinkedIn.com or on any other membership site. Instead, navigate to the site directly by typing in the address bar in your browser.
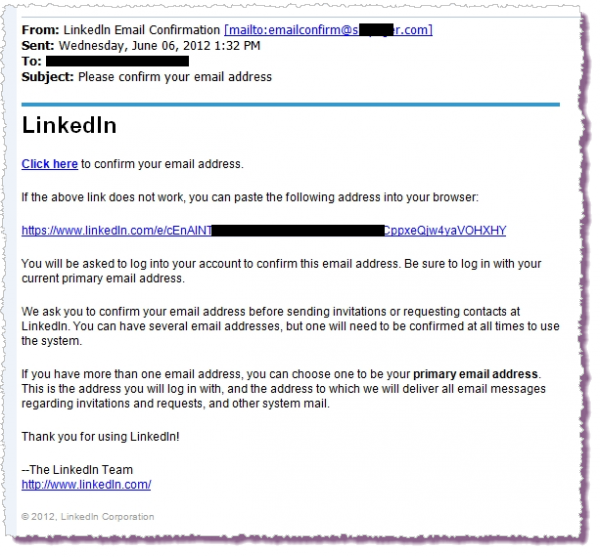
[Note that the first link --"Click here" -- is the one that takes you to somewhere other than LinkedIn. In this case the destination is an illegal online pharmacy selling Viagra and similar products. Because similar emails have been circulating for some time it is hard to say if this is an example of a coordinated scam designed to leverage the security breach made public today, or simply a coincidence (like getting a phishing email asking you to reset your Bank of America online banking password two days after you opened an account there). Sadly, we are likely to see more of these emails as LinkedIn tries to rebuild trust among members.]
Reprinted with permission.
Photo Credit: Feng Yu/Shutterstock.com
 Cameron Camp is a researcher for global security provider ESET and has played a critical role in building the ESET North America Research Lab. Cameron has been building critical technology infrastructures for more than 20 years, beginning as an assembly language programmer in 1987 and eventually becoming an evangelist for Linux and open-source technologies with an emphasis on the security sector. Prior to joining ESET, he founded Logical Web Host in 1998, a data-driven web services company.
Cameron Camp is a researcher for global security provider ESET and has played a critical role in building the ESET North America Research Lab. Cameron has been building critical technology infrastructures for more than 20 years, beginning as an assembly language programmer in 1987 and eventually becoming an evangelist for Linux and open-source technologies with an emphasis on the security sector. Prior to joining ESET, he founded Logical Web Host in 1998, a data-driven web services company.

