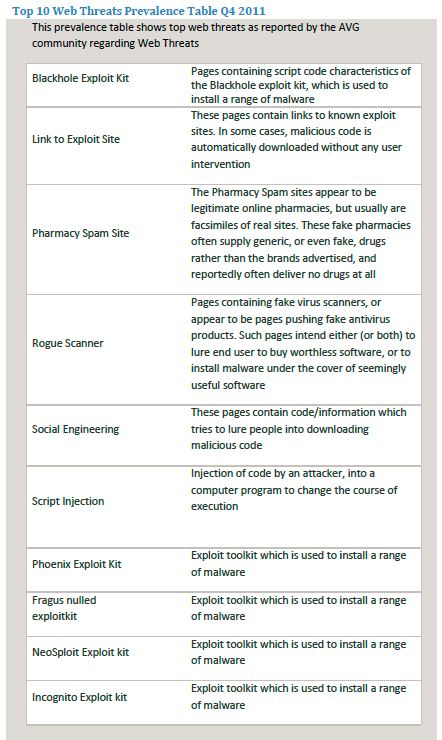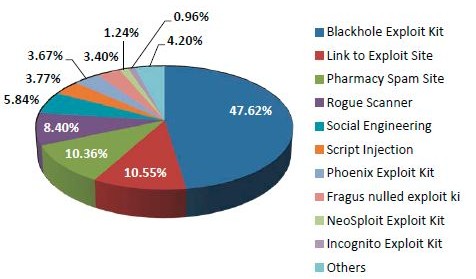
The compromised website is still the most effective attack vector for hackers to install malware on your computer with 47.6 percent of all malware installs occurring in that manner, says security firm AVG. Another 10.6 percent are tricked into downloading exploit code -- many times, without their knowledge -- by clicking on links on pages to sites hosting malware.
The Chelmsford, Mass. company announced its findings as part of a broader study of threats detected by its software. It also found that faked pharmacy sites are a popular attack method, seen in about 10.4 percent of all attacks.
Fake antivirus scanners remain a popular malware injection method at 8.4 percent. The news is timely considering just yesterday Microsoft announced its newest defendant in the Kelihos botnet case was a former antivirus vendor employee. Kelihos used fake antivirus to install itself on unsuspecting victims.
"'Old habits die hard': cyber criminals are up to their old tricks, apparently the use of fake antivirus product is still successful", the firm says in its report. It adds that a significant portion of these rogue antivirus installs are coming through whats called a "Second-Click Redirect Mechanism".
A faked image gallery is a good example. Clicking on the first image will behave as expected, however going back to the gallery and clicking on a second thumbnail will trigger the script. The user is redirected to download antivirus software after a popup claims viruses were "found".
Fake antivirus is nothing new, but this attempt to bury it is: the attackers want it to look more legitimate.
That's not all, though: AVG warns that the security issues plaguing desktops are migrating to mobile devices. "While consumers are going mobile, so are the cyber criminals," the company writes. "We have witnessed the use of the same malicious intent tactics targeting mobile devices: social engineering, stolen or fake certificates to sign malware, rootkits and other tactics".