By Angela Gunn and the Betanews Staff, Betanews
 With hours (if not minutes) to go before President Obama reveals the results of a comprehensive study of federal cybersecurity, consumer gadgets take the stage on a sleepy Friday to cap off a noisy week. We now know, for instance, just how long Sprint's exclusivity over the Palm Pre will last in the US. Did anyone have dibs on six months? No, not even that.
With hours (if not minutes) to go before President Obama reveals the results of a comprehensive study of federal cybersecurity, consumer gadgets take the stage on a sleepy Friday to cap off a noisy week. We now know, for instance, just how long Sprint's exclusivity over the Palm Pre will last in the US. Did anyone have dibs on six months? No, not even that.

It's no longer the "Sprint Pre"
Evening of May 28, 2009 · In a special conference call with reporters yesterday, Verizon Wireless CEO Lowell McAdam announced that the nation's largest wireless carrier will offer the Palm Pre as part of its broader lineup of smartphones. The sequel to the touchscreen BlackBerry Storm will also be in that lineup, said McAdam in comments cited by Reuters this morning.
"Over the next six months or so you will see devices like Palm Pre and a second generation Storm," Reuters quotes McAdam as saying.
Though it may be too early at this stage to gauge reactions, the announcement could only be a major blow to Sprint, more for Verizon's ability to announce it now than for any other reason. While Sprint's network quality in the US has been perceived as improving, it has had to rise from the absolute bottom of the well. Consumers considering a Palm Pre purchase next month have been weighing whether investing in Sprint's network long term will be worth it.
So consumers who do make the jump next month will be those willing to overlook Verizon's leadership in network quality, who are impressed by Sprint's "Everything" calling plan, and who don't want to wait until near-Christmas to own what could still be the coolest device of the summer. But all of a sudden, there are a lot more "if's" for consumers to consider, and Sprint cannot be happy.
Attention shoppers: Empty your wallets
Morning of May 28, 2009 · The consortium that sets the standards for HDMI would really, really appreciate it if you would spend some money already. The group has announced the HDMI 1.4 specification, which adds an Ethernet channel to the cable's capabilities, increases the data-exchange rate, and introduces the ability for the cable itself to optimize the TV image based on the content type. Of course, 1.4 will only work with a bunch of sets and boxes that aren't even on sale yet, so if you want the functionality you should prepare to lay out money for an all-new setup. Fast Company's excited, but the Associated Press could barely stifle a yawn and BusinessWeek's Cliff Edwards correctly notes that many erstwhile shoppers will simply wait until their old gear "conks out."
There's money in computing, we hear
12:43 pm EDT, May 28, 2009 · Via The Consumerist, a report reaches us from St. Louis that a Best Buy customer who dropped his PC off with the Nerd Herd Geek Squad for repairs somehow forgot that he left approximately $10,000 in cash wadded up inside it. Best Buy called the cops, who confirmed that the money was legit. Your reporter suggests that maybe if Scrooge McDuck hadn't used his tower case as a wallet, perhaps the computer wouldn't have needed "repairs" in the first place.
 Friday's tech headlines
Friday's tech headlines
The New York Times
· As your reporter waits (and waits and WAITS) for the White House to finally announce its cyberspace security plans and who the czar will be, the Pentagon's already making plans for a military command for cyberspace. (More on this in What's Next, below.)
· Today's financial-report gloom is brought to you by Ashlee Vance, who digs into Dell's 63% drop in quarterly earnings.
· Everyone's awfully excited about that New Yorker cover the artist created on his iPhone. Gadgetwise looks at four iPhone programs that will let you make art of your own, though a cover spot... let's just agree it's still a long shot.
Los Angeles Times
· Joe Flint and David Sarno deliver a nice analysis of what the AOL-Time Warner breakup means from an entertainment-industry perspective.
· Op-Ed writer Jon Healey detours to the site's tech blog to opine on a new study from the Digital Watermarking Alliance, which presents a case for watermarking as an alternative to DRM technology. That's a dubious tech proposition for various reasons, but Healey cites some interesting stats and links to the report itself if you're curious.
The Register
· Mmm, fresh steganography. Researchers in Warsaw have found a way to send nearly undetectable messages through the Internet by manipulating a design glitch in how TCP confirms packet receipt.
· Wikipedia puts the hammer down in its long-running battle with certain overzealous 'editors" from the Church of Scientology, banning all contributions from IP addresses owned or operated by the Church of Scientology and associated entities. (No, not EarthLink. Stop that.)
· We missed the golden anniversary of monkey spaceflight? We're really just living all wrong here at Betanews. Able and Miss Baker went up and came back (take that, Laika-murdering Russkies!) fifty years ago Thursday.
Wired
· Are you easily distracted, or do your powers of concentration awe and frighten your co-workers? New research indicates that one's ability to focus depends on separate areas of the brain being able to fire in unison. The neuroscience could lead to new treatments for schizophrenia and ADHD.
· Nate Ralph got his product-reviewing hands on the upcoming Sims 3 port to the iPhone, and it looks pretty good. He wishes it had more interaction with the PC version, though.
Technologizer
· Harry McCracken wants to know if we should go ahead and expect Google's Wave to emerge as bloatware.
· Who knew that big hair is verboten in video games? And who knew that this would be a serious problem for video companies hoping to turn famous humans into onscreen characters?
WHAT'S NEXT? Security, as written in the czars...

Security as written in the czars
The story of Google Wave will unfold over the next few months, and down the road we'll all know whether Google's baby is bloatware or the next big revolution in how we compute. Up next, though, you're about to watch the tip of a very large iceberg float by.
Sometime today, the White House will reveal the results of Melissa Hathaway's (more or less) 60-day examination of the current state of federal cybersecurity, and it's believed that today President Obama will name his long-awaited cyberczar. (Your reporter's money is on Hathaway, as long as promptness isn't in the job description.)
If certain agencies of our federal government had applied as much effort to actually doing national cybersecurity as they've put toward fighting over jurisdiction over it, we'd be several orders of magnitude safer today. The two main battlers have been the military and the NSA, in part because the latter agency is forbidden to do spying on US soil but in part because this is Washington and that's what people do.
Neither Mr. Obama's announcement nor the Pentagon's announced plans for a military cyberspace command are going to terminate this turf war, unfortunately. The White House effort is primarily concerned with certain forms of government and civilian infrastructure -- the networks that are too big to fail, if you like. There's no thought that the White House post will involve itself in any sort of offensive cyber-actions.
Which leaves us, again, with the uniforms and the spooks slapping each other around. A concerned observer can't help but be conflicted here. On the one hand, cyberwar is going to operate a lot more like spies do and a lot less like soldiers do, or at least like soldiers have done in the past. A functional cybercommand needs to be light on its feet and flexible in its structure. On the other hand, American spy agencies shouldn't be conducting large-scale warfare; that isn't who we are as a country (note to self: if you believe that, it may be time to re-read A Legacy Of Ashes). And I'm not in favor of the Gordian-knot idea of subsuming the NSA into the military; the prospect reminds me, oddly, of the old Prodigy online service, which wags held to have combined the tech acumen of Sears and the consumer-friendliness of IBM, its two not-so-proud parents.
The NYT article linked above points out that the NSA has most of the current expertise on digital warfare, but the military's becoming extremely serious about wargaming its way to understanding. Today you'll see the tip of that political iceberg float by as the White House nominates its cyberczar, but be aware that a sustained, complex, and bitter struggle for power glides just below the waterline.

Copyright Betanews, Inc. 2009








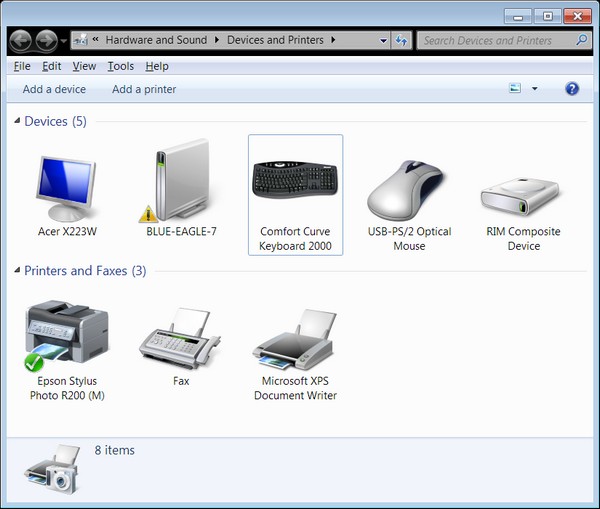
 If the strange feeling that Vista was less secure than XP was topmost on critics' gripe lists over the last three years -- regardless of the facts which contra-indicate that feeling -- running a close second was the feeling that very little, if anything, outside of the PC worked with Vista when you plugged it in.
If the strange feeling that Vista was less secure than XP was topmost on critics' gripe lists over the last three years -- regardless of the facts which contra-indicate that feeling -- running a close second was the feeling that very little, if anything, outside of the PC worked with Vista when you plugged it in.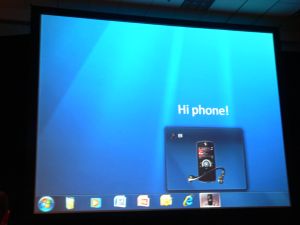 Since the Windows 7 taskbar itself has changed since that initial prototype was presented, the concept has evolved a bit, and in a sense simplified. Now when you plug in a recognized device, an icon for it does appear in the new taskbar, and it can be "pinned" there just like an application. Hovering over it brings up a frame that can serve as a status report for the device -- for instance, registering the battery level for a phone or a camera, or showing how many songs are loaded in an MP3 player and how many minutes or megabytes remain.
Since the Windows 7 taskbar itself has changed since that initial prototype was presented, the concept has evolved a bit, and in a sense simplified. Now when you plug in a recognized device, an icon for it does appear in the new taskbar, and it can be "pinned" there just like an application. Hovering over it brings up a frame that can serve as a status report for the device -- for instance, registering the battery level for a phone or a camera, or showing how many songs are loaded in an MP3 player and how many minutes or megabytes remain.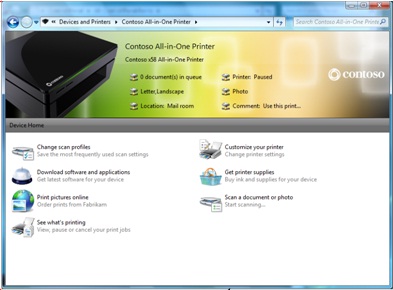 What Microsoft is hoping manufacturers will embrace is a concept called the
What Microsoft is hoping manufacturers will embrace is a concept called the 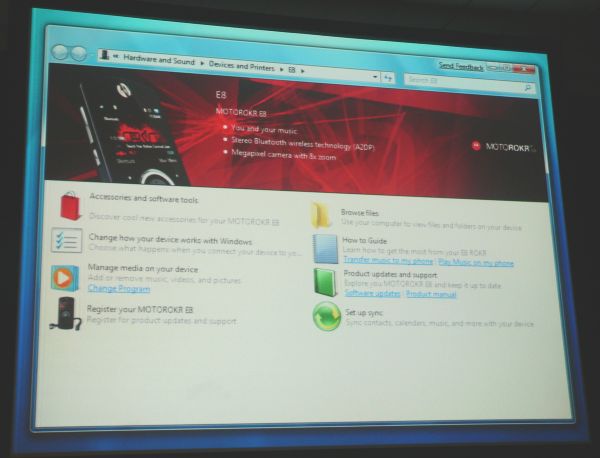


 With hours (if not minutes) to go before President Obama reveals the results of a comprehensive study of federal cybersecurity, consumer gadgets take the stage on a sleepy Friday to cap off a noisy week. We now know, for instance, just how long Sprint's exclusivity over the Palm Pre will last in the US. Did anyone have dibs on six months? No, not even that.
With hours (if not minutes) to go before President Obama reveals the results of a comprehensive study of federal cybersecurity, consumer gadgets take the stage on a sleepy Friday to cap off a noisy week. We now know, for instance, just how long Sprint's exclusivity over the Palm Pre will last in the US. Did anyone have dibs on six months? No, not even that.
 Friday's tech headlines
Friday's tech headlines 
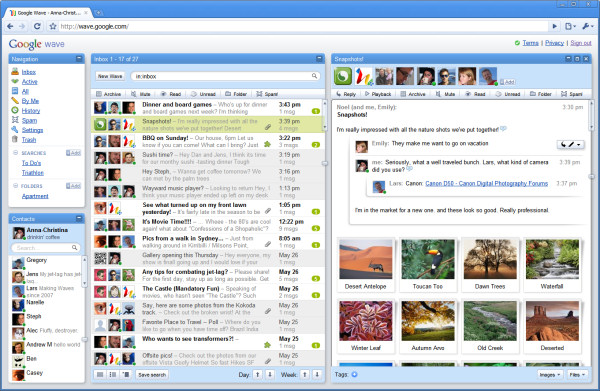
 It's not unusual to see something emerging from Google's laboratories that folks in the general press fail to understand, and the company's marketing is partly to blame there. The public introduction during this morning's I/O Developers' conference of a Web programming construct called Google Wave generated headlines ranging in scope from a new competitor for Microsoft SharePoint, to a next generation social network, to a series of browser extensions for Chrome to rival
It's not unusual to see something emerging from Google's laboratories that folks in the general press fail to understand, and the company's marketing is partly to blame there. The public introduction during this morning's I/O Developers' conference of a Web programming construct called Google Wave generated headlines ranging in scope from a new competitor for Microsoft SharePoint, to a next generation social network, to a series of browser extensions for Chrome to rival